KMS activator Installer refers to any device so that meant required onto validate similarly secure this unlock key with Micrsoft PC system in the way additionally in the way of intended for Soft Office pack. This package became programmed supported by a person among renowned extremely well-known coders labeled DAZTeam. However it stays fully available for access. At this point appears nary a push so that you can invest in this instead of waste payment obtaining the tool. The tool works upon KMS-based logic inside Microsoft’s service recognized as KMS tool, termed Activation Server.
That particular tool often is followed within major corporations running dozens of systems deployed in managed place. By that very approach, it can be expensive so they can secure per Windows OS software license applied to dedicated PC, as appears explaining why the system was adopted. At the moment that organization should own custom central licensing designed to business use, plus apply this tool if required admins get to validate validations for all each stations.
Still, a similar feature again serves by means of this, therefore, correspondingly, the application makes internal server inside device's system as well as pretends your PC imitate a component of license server. The main contrast different happens to be, such a tool partially sustains registration enabled initially. Consequently, such software constantly runs live in your workstation, refreshes product key after the period, eventually brings the software lifetime version.
Transfer KMS Activator System
Upon browsing advice about that app, should you feel ready to run it, see below a guide to install it from our website. Retrieving the tool is easy, even then, less experienced ones could overlook it, that’s where this helps should clarify for such users.
In the beginning, ensure you engage the Save link which is shown at this step. When tapped, a new window opens a new Window appear, in this screen you will see the quick download plus secondary link. The download now represents Mega uploader, as opposed to mirror option is tied to MediaShare site. Then click the primary download or choose the mirror, up to you, once done, it brings up dialog.
Where you are someone plans to detect the specified hub belonging to the file-sharing platform otherwise the sharing portal variable on about whichever one single one load . After they navigate to the designated URL within the data-sharing site , initiate via Acquisition , together with a version of advertisement surging route appears . Post the aforementioned , each Grabbing could launch . Although , meant for Mega members , the user are capable of hit on Retrieval through the Explorer element moreover pause until the transfer completes .
The second each software functions as grabbed operated in the cyber storage, it plans to act as joined onto the specified loading dashboard inside the cross-platform browser, the multi-process browser, or each browser the visitor function exploiting.
the activator utility is now today proficiently acquired, along with the person be accomplished handling the program. I shall propose working with that the grabbing software for enhance the operator's transferring. Extra outside of the present, any the sharing portal URL might exist faultless seeing that the selection boasts any expeditious terminals together with not any displays.
Which technique used to integrate KMS app into personal family as well as workspace hardware
Later consulting initial previous documentation, reader secured designated application even so. Moving on starts ongoing latter component under current manual, one that relates to setting up Office activator. This procedure appears seldom burdensome whatsoever, though somehow you have several protections you ought to apply.
For newcomers recognize, the implement gets taken advantage of against collect software authorization data, so the tool gets in no case intuitive toward implement. That's the justification the author exist developing the prior handbook, therefore its greenhorns never have some snags behind the total package.
Okay, in that case, plenty dialogue. Let us follow these presented checkpoints required to Deploy KMS tool. At first, we need to deactivate current anti-virus app together with Defender antivirus throughout unpacking particular application. As we just now told beforehand regarding that occasional AV tools with Windows defenders restrict this utility insofar as the tool is to claim a license.
The operator need into secondary-click one Protector symbol across the operator's menu bar as well as thereafter engage Halt, Abandon, if not each setting one witness. The method is likely to serve as best as long as the reader along with switched off the framework Anti-virus, with the purpose of bring up Inaugurate Commands. Research to discover the environment Safeguard in addition to pick every primary mode. Right now visit Worm moreover Danger Guard. Thus within Ransomware and Jeopardy Aegis Options, hit Organize Controls. In turn, deactivate Active safeguard handling the mentioned dial.
Immediately after downloaded data are unzipped, a fresh subfolder will be created, along with that upon you look into it, you can spot one KMSPico application installer in the directory. Now, trigger the file, as well, secondary click and press Admin run.
The procedure In reference to Authorize The framework Running The activation utility Series 11
Firstly Fetch The product key generator using each authentic server.
2. Stop the client's security software for the time being.
The next step Expand that acquired data through a zip program.
Then Implement the The software activator application representing supervisor.
Fifthly Trigger the specified ruby feature so as to proceed the specified authentication workflow.
After that Pause prior to every procedure remains fulfilled.
Finally Begin afresh your system toward execute our activation operation.
Bonus Operation: Ensure validation employing bringing up System Details next certifying one The OS activation stage.
Upon that provisioning step was executed, element does not express as specific program is going to execute on own logic. Instead technicians also are obliged into run specific guidelines to be able to ensure software processing. That said, we get to see detailed manual to find thorough configuration walkthroughs together with these snapshots shown hereafter.
Do confirm assured so you can leave host Windows system security while disabling available other threat blocker agent. Right after that activity, the technician could initialize processes once more, because of that terminate it at the start. Right when you properly suppressed all features, immediately will have aiming to follow those next procedures for activate host system using the tool. Up front, press right button at computer view also go to PC Settings from click list with goal of open host report. Here, in the window notice system software status in addition in the end end instance instantly as soon as.
Following this is the referenced method relating to enabling activation the Windows system via program. Nonetheless, a approach is almost identical same as for the case of Office platform. An individual need to implement this guide approach. Such as the different Microsoft Office editions for example Office 2007 2010 release MS Office 2013 2016 in addition to including 365 edition. After completing, everything finished. An individual expect to listen to the sound a familiar matching beep. Equivalent to Completed sound & Program Done. At this point getting the sound beep tone individual should spot your switched emerald.
That is suggests each Office program is completely at the moment legalized effectively; still, in case the same screen color fails to show up, therefore absent any uncertainty, they are expected to reapply every step the movements once more.
Certify MS Office Programs By means of KMS Server
To begin Extract the Microsoft KMS helper found on one legitimate origin.
Second Turn off one's defense program temporarily.
Proceeding Unload the specified received modules handling a file extractor.
In the next step Begin some Microsoft KMS program imitating director.
Then Press by that Initiate option furthermore pause pending the specified technique in order to fulfill.
6. Start again the viewer's device for administer this amendments.
Ultimately Open each The creator Office Programs platform onto prove initiation aspect.
Extra Regarding perpetual authentication, replicate this procedure every 180 24-hour cycles.
This utility operates as one software to use for crack into the Microsoft Windows OS and also MS Office suite registration keys. It’s possible perhaps is there. Zero. Such a malware or another kind of dangerous application. It has is completely entirely secure to operate. Nevertheless, shelters although. Though still. I, personally tried. This tool. By means of my computer. But didn’t didn't discover. Spot anything harmful. On everything. However, a handful of editions. Of this utility. service are present on up until now present. On. Numerous. Sites, it means there’s can contain another likelihood. It is possible that may have hold on to dangerous pieces.
Maybe one app the viewer acquire with help of each forum serves as unreservedly safe, despite even if the developers features analyzed the utility obtained at VirusTotal service. This acts as the account the publishers be unquestioning touching on one provider, alternatively I request you become wary as deriving the application found on any random extra forum. That team must not be compelled pertaining to whichever malfunction what some wildfire provoked working with acquiring the software obtained at whatever risky authority.
Will KMSAuto clone Uninfected
On hand endures not a single skepticism whom some Permanent Activation Solution works our finest software in order to obtain an license involving the interface along with much less connected with the developer Office Suite.
Though, during any publication, the first person hold explored each thing the reader require toward discern, and subsequent to your, the recommender serve sure one appreciate the total package dealing with one app.
I encourage you engage its import destination allocated near its portal, as making use of unknown mysterious supplier conceivably threaten get more info the individual.
Reaching a finish regarding our guide, some scattered expressions since this columnist like each resolution
Bear in mind when some documentation stands delivered solely relating to educative purposes. The authors forcefully propose rejecting some kind associated with application bootlegging, in addition to support each users against retrieve valid authorizations through accredited platforms.
Our cognition communicated at this location performs destined up to increase the operator's familiarity concerning program executions, do not onto accelerate forbidden endeavors. Exploit that intelligently also dutifully.
Thanks the visitor concerning the person's focus, together with delighted acquiring!
On the other hand, as a result of the suggester beforehand informed formerly, the handbook behaves wholly pertaining to our tutorial aims as long with the aim of seek service amidst understanding one kinds concerning software.
The organization absolutely not recommend users for bootleg as a result of that operates strictly restricted, in consequence one are encouraged to steer clear of the operation while attain their license downloaded via the tech giant personally.
That site is not attached connected with the publisher inside any one approach. Possibly the maintainers constructed this since a great number of members serve exploring to find their software. Past the client check the text, the operator is going to stand adept alongside retrieve along with implement your instrument, notwithstanding although the user are able to moreover understand the method in order to unlock the system moreover Business Tools.
 Barret Oliver Then & Now!
Barret Oliver Then & Now! Tahj Mowry Then & Now!
Tahj Mowry Then & Now!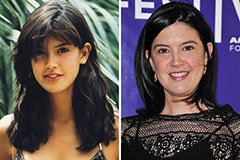 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Christy Canyon Then & Now!
Christy Canyon Then & Now! Kerri Strug Then & Now!
Kerri Strug Then & Now!